SHARE THIS ARTICLE
Security Tokens vs. Utility Tokens: Understanding the Difference1
Blockchain technology, with its new models of trust and transparency, has disrupted industries. A key innovation within this space is tokenization – the process of representing real-world assets or functionalities as digital tokens on a blockchain. These tokens can range from simple digital representations of value to complex instruments with financial implications.
There are two primary categories of tokens – security tokens and utility tokens. While both utilize the underlying technology of blockchain, their fundament purposes, regulatory frameworks, and investor protections are considerably different.
It is vital to understand the difference between the two token types for all stakeholders, including investors, developers, and regulators. This knowledge is instrumental in making informed decisions, eliminating risks, and decoding the complexities around digital assets.
All About Security Tokens
A security token is a digital representation of a financial asset or security. It is a cryptographic token issued on a blockchain platform that signifies ownership or investment in an underlying asset. Security tokens do not offer access to a product or service but rather are subject to securities regulations and provide investors with financial rights and expectations.
How Do Security Tokens Work?
When an asset is tokenized, it is divided into smaller units, each represented by a security token. These tokens can be traded on secondary markets, offering investors the opportunity to buy, sell, or hold their digital assets. The underlying asset can be anything from real estate to stocks, bonds, or even intellectual property. This process of fractional ownership allows for broader participation in investment opportunities. Moreover, the blockchain technology underlying security tokens provides a transparent and immutable record of ownership, ensuring the security and integrity of the investment.
Types of Assets That Can Be Tokenized
An extensive range of assets is suitable for tokenization. Here are some common examples.
-
Real Estate: Property can be fractionalized into security tokens, allowing investors to own a portion of a building or property portfolio.
-
Equities: Shares of private or public companies can be represented as security tokens, providing investors with ownership rights and potential dividends.
-
Debt Securities: Bonds, loans, and other debt instruments can be tokenized, offering investors fixed income returns.
-
Commodities: Physical assets like gold, oil, or agricultural products can be tokenized, providing investors exposure to commodity prices.
-
Intellectual Property: Patents, trademarks, and copyrights can be tokenized, allowing investors to participate in the potential revenue generated by these assets.
Types of Assets That Can Be Tokenized
An extensive range of assets is suitable for tokenization. Here are some common examples.
-
Real Estate: Property can be fractionalized into security tokens, allowing investors to own a portion of a building or property portfolio.
-
Equities: Shares of private or public companies can be represented as security tokens, providing investors with ownership rights and potential dividends.
-
Debt Securities: Bonds, loans, and other debt instruments can be tokenized, offering investors fixed income returns.
-
Commodities: Physical assets like gold, oil, or agricultural products can be tokenized, providing investors exposure to commodity prices.
-
Intellectual Property: Patents, trademarks, and copyrights can be tokenized, allowing investors to participate in the potential revenue generated by these assets.
Regulatory Framework for Security Tokens
The regulatory environment surrounding security tokens is complex and varies across jurisdictions. In many countries, security tokens are subject to the same rules and regulations as traditional securities. This means that issuers of security tokens must comply with securities laws, including registration requirements, investor disclosures, and ongoing reporting obligations.
For instance, in the United States, the Securities and Exchange Commission (SEC) has asserted its authority over security tokens, requiring issuers to adhere to securities laws. Additionally, security token platforms and intermediaries must implement robust Know Your Customer (KYC) and Anti-Money Laundering (AML) procedures to prevent financial crime.
Advantages of Security Token Offerings (STOs)
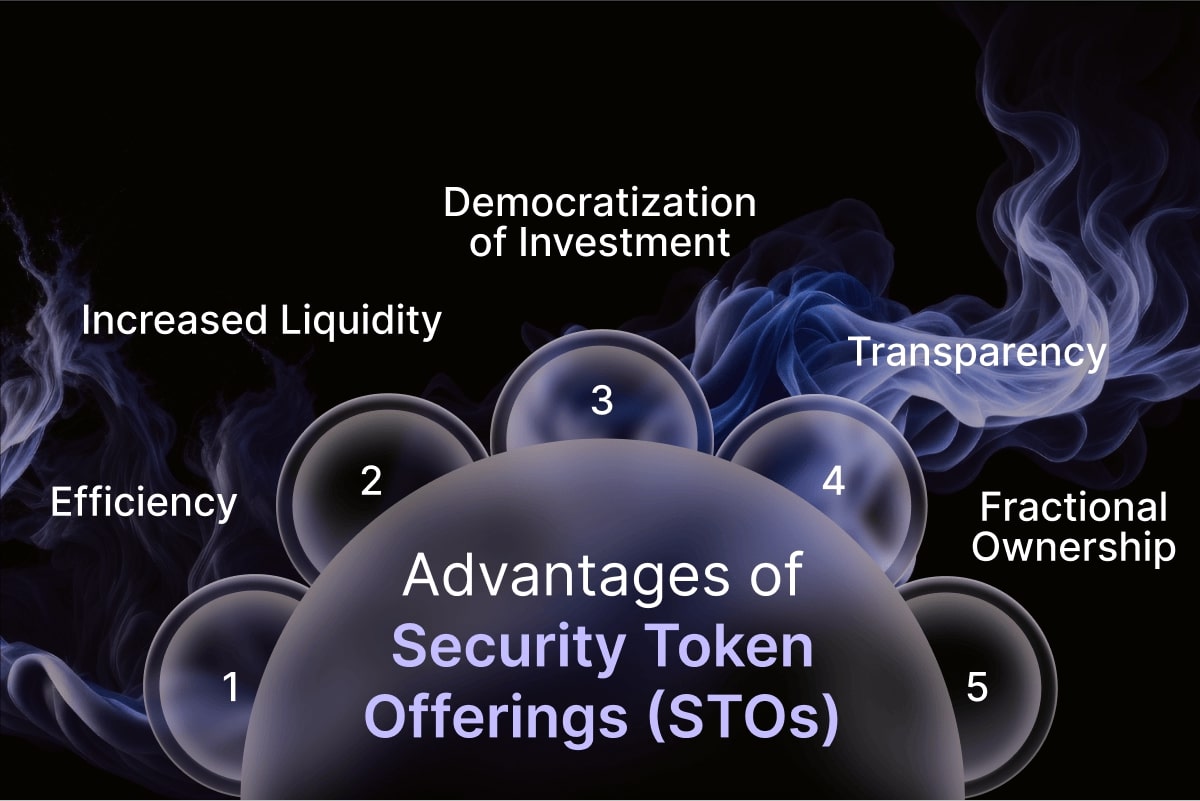
Security token offerings (STOs) present several potential advantages over traditional securities offerings.
-
Efficiency: The issuance process for security tokens can be more efficient and cost-effective compared to traditional securities offerings, reducing time and expenses.
-
Increased Liquidity: STOs can provide increased liquidity for investors by facilitating trading on secondary markets, allowing them to buy and sell their tokens more readily.
-
Fractional Ownership: Security tokens allow for fractional ownership of assets, making investments accessible to a wider range of investors.
-
Transparency: The blockchain technology underlying security tokens provides a transparent and auditable record of ownership and transactions, promoting investor trust.
-
Democratization of Investment: STOs can democratize access to investment opportunities by allowing individuals to invest in assets that were previously reserved for institutional investors.
Challenges and Risks Associated with Security Tokens
While security tokens offer numerous advantages, it's essential to acknowledge the challenges and risks involved.
-
Regulatory Uncertainty: The regulatory frameworks for security tokens are still nascent in many jurisdictions. This uncertainty can create challenges for issuers and investors alike, as compliance requirements may change over time.
-
Market Volatility: The value of security tokens can fluctuate considerably due to market conditions, economic factors, and investor sentiment. This volatility poses risks for investors seeking stable returns.
-
Liquidity Risk: While security tokens can potentially offer increased liquidity compared to traditional securities, there's no guarantee of a liquid market for all tokens. This can impact an investor's ability to sell their tokens at a desired price.
-
Counterparty Risk: As with traditional securities, there's counterparty risk in security token investments. The issuer of the token may default on its obligations, leading to financial losses for investors.
-
Custody and Security Risks: The safekeeping of digital assets, including security tokens, requires efficient security measures. The loss or theft of private keys can result in the loss of tokens and investor funds.
-
Valuation Challenges: Accurately valuing underlying assets that are tokenized can be complex, especially for assets with illiquid markets. This can impact the fair pricing of security tokens.
-
Investor Protection: While regulations are evolving, investor protection measures for security token holders may not be as effective as those for traditional securities in some jurisdictions.
It is crucial for investors to conduct thorough due diligence and understand the risks associated with security tokens before making investment decisions.
Understanding Utility Tokens
A utility token is a digital asset that provides access to goods or services within a specific platform or ecosystem. Unlike security tokens, which represent ownership in an underlying asset, utility tokens are primarily functional. They typically do not offer financial returns to investors and are not subject to the same securities regulations.
How Do Utility Tokens Work?
The value of a utility token is derived from its utility within the platform it supports. Token holders can use them to access features, pay for services, or participate in platform governance. This creates a symbiotic relationship between the token and the platform, as the token's value is often tied to the success and growth of the ecosystem.
Use Cases of Utility Tokens
-
Payment Tokens: Utility tokens can serve as a medium of exchange within a platform, allowing users to purchase goods or services. Examples include tokens used for online purchases, in-game transactions, or digital content consumption.
-
Access Tokens: These tokens grant holders access to exclusive features, content, or services. For instance, a streaming platform might offer premium content to users who hold a certain number of platform tokens.
-
Governance Tokens: Utility tokens can be used to grant holders voting rights in platform decision-making. This encourages community involvement and allows token holders to influence the platform's development.
-
Loyalty and Rewards Tokens: These tokens can be used to reward customer loyalty or incentivize specific behaviors. For example, a retailer might offer discounts or exclusive offers to customers who hold their loyalty tokens.
Regulatory Landscape for Utility Tokens
The regulatory environment for utility tokens is less defined compared to security tokens. In many jurisdictions, they are not considered securities, providing issuers with greater flexibility. However, it's essential to note that the regulatory frameworks are still evolving, and there are potential gray areas.
Some jurisdictions have implemented specific regulations for initial coin offerings (ICOs), which are often used to distribute utility tokens. Both issuers and investors must stay informed about the applicable regulations to avoid legal issues.
Utility Token Offerings (ICOs and TGEs)
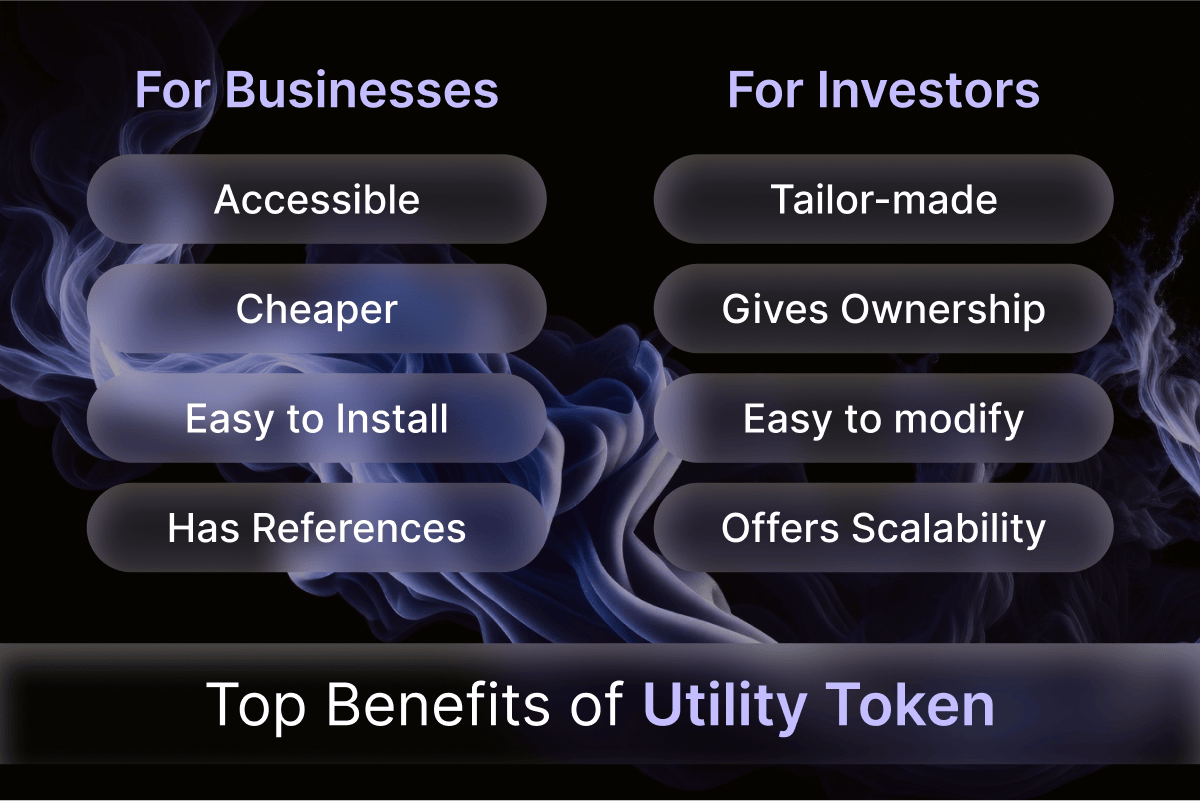
Initial Coin Offerings (ICOs) and Token Generation Events (TGEs) are methods used to raise funds for blockchain projects by distributing utility tokens to investors in exchange for digital or fiat currency.
Advantages of ICOs and TGEs
-
ICOs and TGEs can be a swift way to raise capital for blockchain projects.
-
These offerings can attract investors from around the world.
-
ICOs can help create a strong community around a project.
Disadvantages of ICOs and TGEs
-
The regulatory environment for ICOs is uncertain, exposing projects and investors to legal risks.
-
The price of utility tokens can be highly volatile, impacting investor returns.
-
There is a risk of project failure, leading to loss of investment.
The Role of Utility Tokens in the Blockchain Ecosystem
Utility tokens play a crucial role in the development of the blockchain ecosystem. They facilitate the creation of decentralized applications (dApps) and promote innovation by providing a means for projects to engage with their communities and incentivize user participation. As the blockchain industry continues to mature, the role of utility tokens is likely to expand, driving the development of new and exciting platforms.
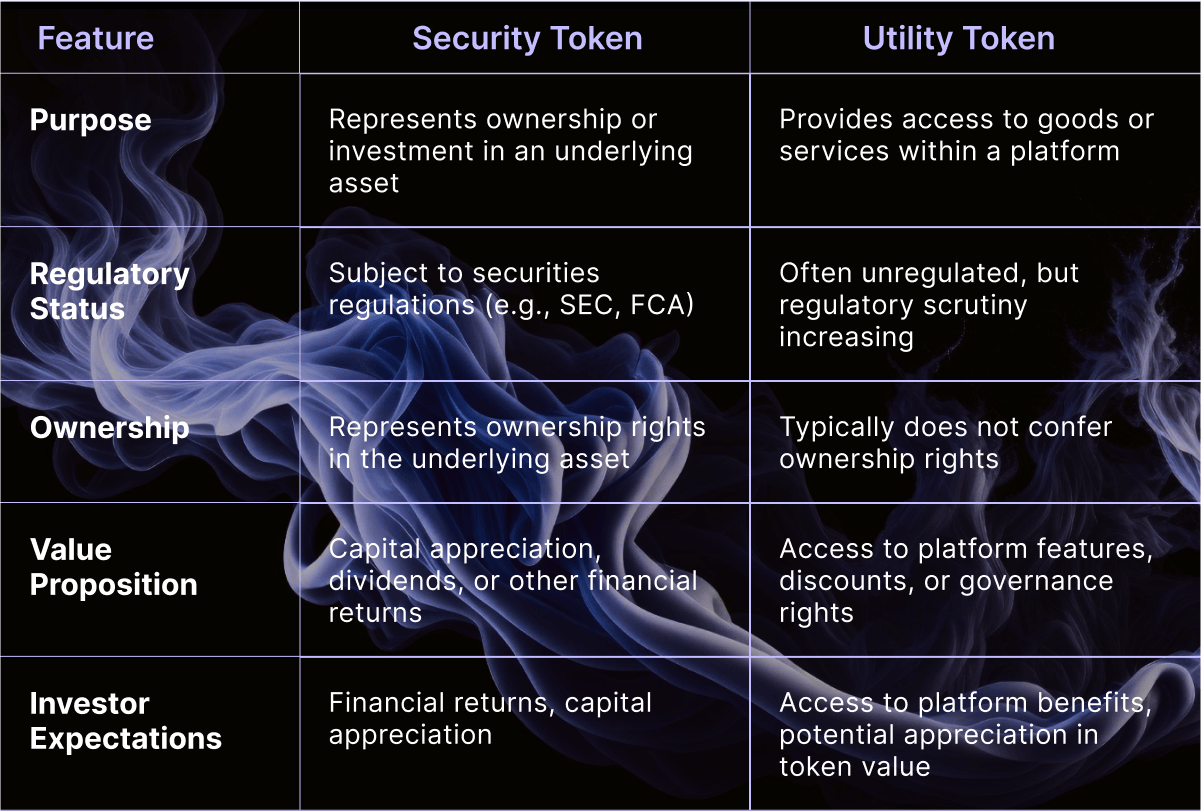
Key Differences Between Security and Utility Tokens
Security and utility tokens, while both digital assets built on blockchain technology, serve distinct purposes and are subject to different regulatory frameworks.
In-Depth Analysis
Purpose and Function
-
Security Tokens: These digital assets are designed to mirror traditional securities, granting investors ownership rights in a company, property, or other asset. Their value is intrinsically tied to the performance of the underlying asset.
-
Utility Tokens: These tokens offer access to a platform's products or services. They are akin to digital vouchers or membership cards, granting holders specific privileges within a defined ecosystem.
Investor Profile and Expectations
-
Security Tokens: Investors in security tokens typically seek financial returns, such as capital appreciation or dividends. They expect to share in the profits or losses of the underlying asset.
-
Utility Tokens: Investors in utility tokens are primarily interested in accessing platform features or services. While the token's value might fluctuate, its primary purpose is to avail platform benefits.
Legal and Regulatory Environment
-
Security Tokens: Due to their investment contract nature, security tokens fall under the purview of securities regulations. Issuers and platforms must adhere to strict compliance standards, including registration, disclosure, and investor protection measures.
-
Utility Tokens: The regulatory landscape for utility tokens is less clear-cut. While many jurisdictions consider them outside the scope of securities laws, the line between security and utility tokens can be blurred.
Token Economics
-
Security Tokens: The economics of security tokens are closely linked to the financial performance of the underlying asset. Token value is influenced by factors such as dividends, asset appreciation, and market demand.
-
Utility Tokens: Utility token economics are driven by platform usage and adoption. Token value can fluctuate based on factors like platform growth, token utility, and supply and demand dynamics.
Use Cases and Applications
-
Security Tokens: Security tokens are suitable for tokenizing various assets, including real estate, equities, debt, and commodities. They can be used for fractional ownership, investment platforms, and asset-backed securities.
-
Utility Tokens: Utility tokens find applications in a wide range of industries, including gaming, supply chain management, loyalty programs, and decentralized finance (DeFi). They are used to create platforms, incentivize user participation, and facilitate transactions.
Real-World Examples
To illustrate the practical applications of security and utility tokens, let's examine some prominent projects.
Security Token Projects
Propellr has successfully tokenized commercial real estate assets, allowing investors to participate in high-potential projects with fractional ownership. This innovative platform democratizes access to commercial real estate, previously exclusive to institutional investors.
Platforms such as OpenFinance have facilitated equity tokenization, allowing companies to raise capital through tokenized shares. This approach can optimize fundraising processes and provide investors with increased liquidity.
Utility Token Platforms
Platforms like Uniswap, Compound, and MakerDAO have tapped into utility tokens to create decentralized financial systems. These platforms offer a range of financial services, from lending and borrowing to trading and derivatives.
Axie Infinity, a popular play-to-earn game, utilizes utility tokens to create a virtual economy where players can earn rewards by playing the game. This model has attracted significant attention and investment.
Hybrid Token Case Studies
While the distinction between security and utility tokens is often clear-cut, some projects blur the lines. For instance:
-
Telegram's Gram: Initially conceived as a utility token, Gram was later classified as a security by the SEC due to its investment contract nature. This case highlights the challenges regulators face in categorizing hybrid tokens.
-
Certain Initial Coin Offerings (ICOs): Some ICOs have raised funds by issuing tokens that combine elements of both securities and utilities. While these projects might have initially marketed their tokens as utility-based, their economic structure often resembled investment contracts.
Final Takeaway
The distinction between security and utility tokens is critical for investors, entrepreneurs, and regulators. Misclassifying a token can lead to severe legal and financial consequences. A clear understanding of each token type's characteristics, regulatory frameworks, and potential risks is essential for making informed decisions.
Looking ahead, we can expect to see a proliferation of innovative token-based projects. The convergence of finance and technology will likely create new opportunities and challenges.
At Codezeros, our team of experts can provide comprehensive guidance on:
-
Token classification and regulatory compliance
-
Security token offerings (STOs)
-
Utility token development and launch
-
Token economics and valuation
Whether you're exploring a security token offering, developing a utility token-based platform, or seeking guidance on regulatory compliance, we are here to assist you. Contact us today to learn how we can support your tokenization project.
Post Author
Vivek is a passionate writer and technology enthusiast with expertise in blockchain development. As the lead writer for Codezeros, he aims to educate and inform readers about the potential of blockchain technology and simplify complex concepts to present them in an engaging manner for both technical and non-technical readers.
Differentiate your security and utility token strategy with expert insights from Codezeros.
Security tokens are investment-backed assets; utility tokens drive ecosystem utility. Codezeros ensures your token model is compliant, secure, and aligned with your project’s vision. From legal frameworks to smart contracts, we’ve got you covered.



