SHARE THIS ARTICLE
Zero-Knowledge (ZK) Credentials: A Privacy-First Approach to Web3 Identity

For all its promise of decentralization and self-sovereignty, Web3 still hasn’t cracked one thing: identity.
The idea that users control their own data sounds great—until you try to log in, prove who you are, or verify basic details without relying on centralized platforms. Traditional identity systems just don’t fit the ethos of Web3, and yet, without them, we can’t build secure or compliant applications.
This is where the conversation around privacy-preserving identity starts to matter, and where zk credentials step in. Using zero knowledge proofs, zk credentials let users prove things about themselves without revealing the underlying data. Want to prove you’re over 18, without sharing your birthdate? zk credentials make that possible.
As the push for Web3 identity grows, especially in areas like DeFi, DAOs, and tokenized real-world assets, zero-knowledge systems offer a way to keep user data safe without compromising on transparency or trust.
In this blog, we’ll explore what zk credentials are, how they work, and how your project can integrate them with the help of expert blockchain development services.
What Are Zero-Knowledge Credentials?
Zero-knowledge credentials are digital proofs that let you verify something about yourself without actually revealing the information behind it. It sounds like magic, but it’s just smart cryptography.
In a typical identity system, you’re asked to show your full name, date of birth, and address, even when only one piece of that data is needed. Want to prove you're over 18? Most systems will ask for your ID and expose all kinds of unnecessary information.
zk-based identity systems flip this around. They use zero-knowledge proofs to confirm facts, like your age, citizenship, or membership, without showing any of the raw data. You don’t reveal your birthdate, just a mathematical proof that confirms you meet the requirement.
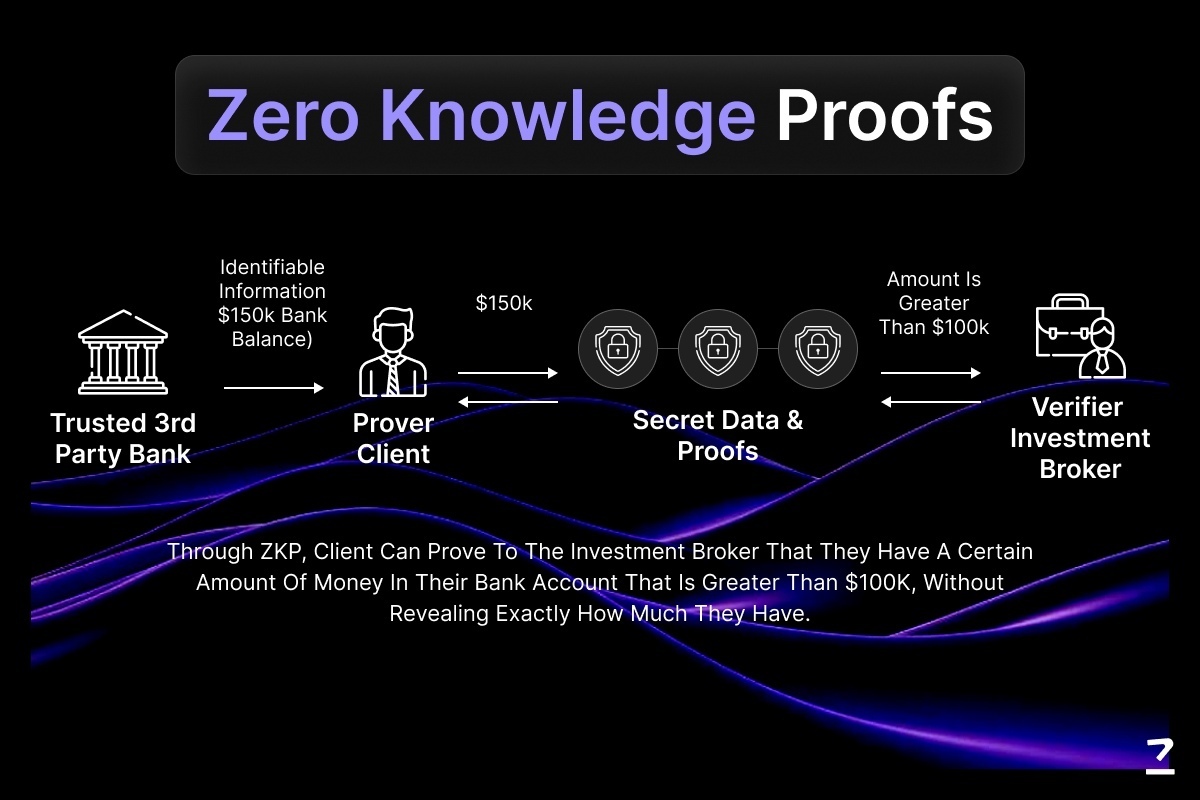
This makes privacy-preserving credentials ideal for Web3. Whether it’s accessing gated content, voting in a DAO, or participating in a token sale, users can now verify eligibility while keeping control over their personal information.
Imagine logging into a decentralized platform and proving you are a valid participant, but nothing about you is stored, shared, or exposed. That’s the power of zk identity verification. It’s secure, anonymous, and designed for systems where trust and privacy go hand in hand.
The Role of Zero-Knowledge Proofs in Identity Systems
At the core of zk credentials is a clever bit of math called a zero-knowledge proof. Simply put, it lets someone prove they know something, without revealing what that something is.
Two common types of these proofs are zk-SNARKs and zk-STARKs. Both allow for fast and private verification, but they differ in how they are built and the kind of cryptographic assumptions they rely on. You don’t need to be a cryptographer to use them. You just need to understand what they make possible.
With zk knowledge proofs, you can verify a user’s identity or qualifications without ever storing or sharing the underlying data. That is a big shift from the usual approach, where sensitive information is exposed and stored across multiple platforms.
This is especially useful in areas like authentication, access control, and KYC. For example, you can let a user into an age-restricted platform without asking for their ID. You can verify that someone is a citizen of a country without seeing their passport. This is zero knowledge authentication in action.
In Web3, where trust is built on code and transparency, zk cryptography allows identity to be secure without becoming a surveillance tool. It creates a model where verification happens, but privacy stays intact.
Why Web3 Needs Privacy-First Identity Models
Web2 identity systems were never designed with user control in mind. They are built around platforms collecting, storing, and monetizing your data. In the world of Web3, that model does not just feel outdated—it becomes a liability.
When you try to use Web3 identity management tools that mimic Web2 models, you run into the same old problems. Surveillance, unauthorized data sharing, and massive data leaks are still possible if your personal information is exposed or stored on-chain.
Some projects have tried to fix this by putting identity directly on the blockchain, aiming for transparency. But full on-chain identity transparency is risky. Once your data is public, it is public forever. There is no going back. You might protect access with keys or encryption, but the data still exists for anyone to see or misuse.
That is why the focus is shifting toward privacy-first models like self-sovereign identity (SSI) and decentralized identity using zk proofs. SSI gives users full ownership of their identity data, while zk-based identity systems go a step further. They let users prove claims without even revealing the data itself.
This model of user-controlled identity is more aligned with the values of decentralization. It gives people the power to interact with platforms, services, and communities without handing over sensitive details every time.
In Web3, privacy is not a bonus feature. It is a basic requirement. And zero knowledge offers a path where identity can finally work without putting users at risk.
How ZK Credentials Work in Practice
Now that we understand why privacy matters in Web3 identity, let’s break down how zk credentials actually work behind the scenes.
At the center of the process is a simple flow: Issuer → Holder → Verifier.
-
The Issuer is the trusted party that creates and signs a credential. Think of this as a university, government body, or any organization that can verify a fact about you.
-
The Holder is you. You receive the credential and store it in a digital wallet.
-
The Verifier is a dApp, DAO, or any platform that needs to confirm your identity or status.
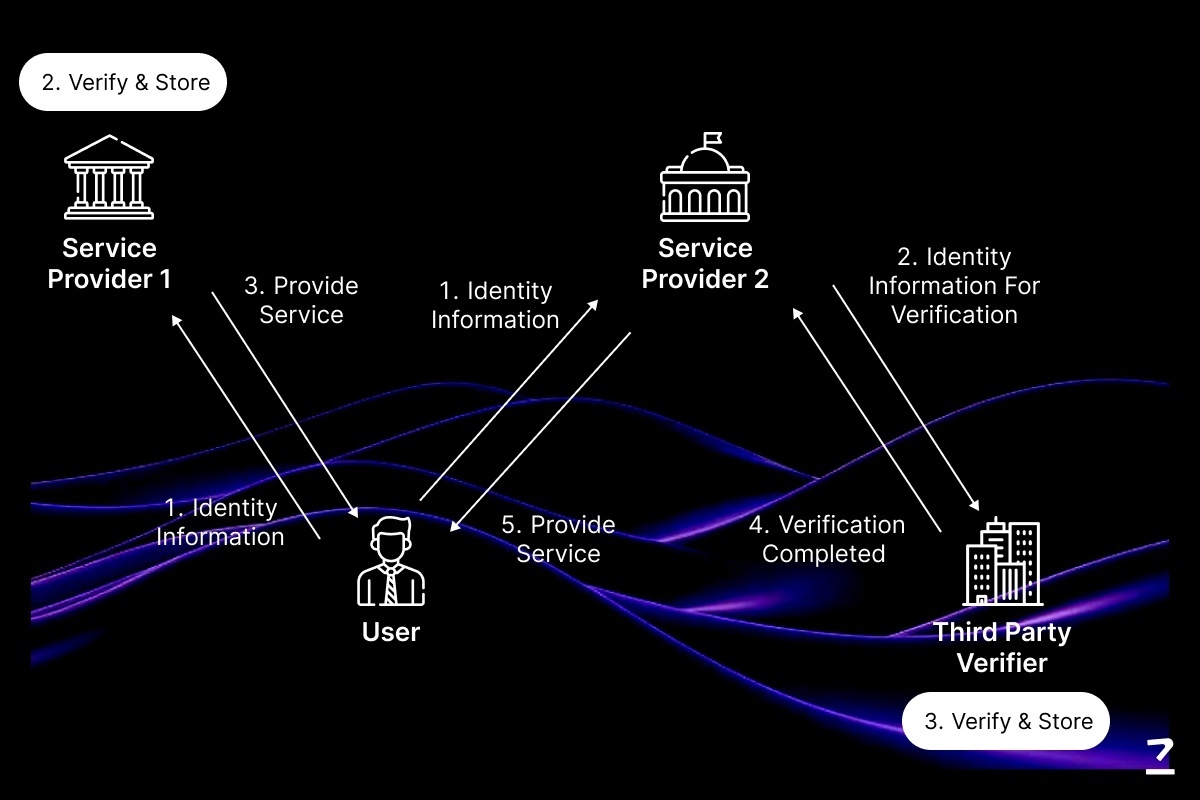
This is where zk-based authentication steps in. Instead of handing over the entire credential, the holder shares a zero knowledge proof that verifies the claim, like age, citizenship, or access rights, without exposing any raw data.
This model is usually built on the Verifiable Credentials architecture. It works alongside DIDs (Decentralized Identifiers), which allow users to prove who they are without relying on a central database. These identifiers are stored securely in a wallet and can be verified on-chain using cryptographic proofs.
Smart contracts often manage the verification logic. They check the zk proof submitted by the holder and return a simple yes or no result to the verifier. No sensitive data is stored, and the verification is both fast and trustless.
This is what makes zk credentials a powerful decentralized identity solution. They provide secure and selective access without compromising user privacy. For anyone building digital identity in Web3, this is the model to watch.
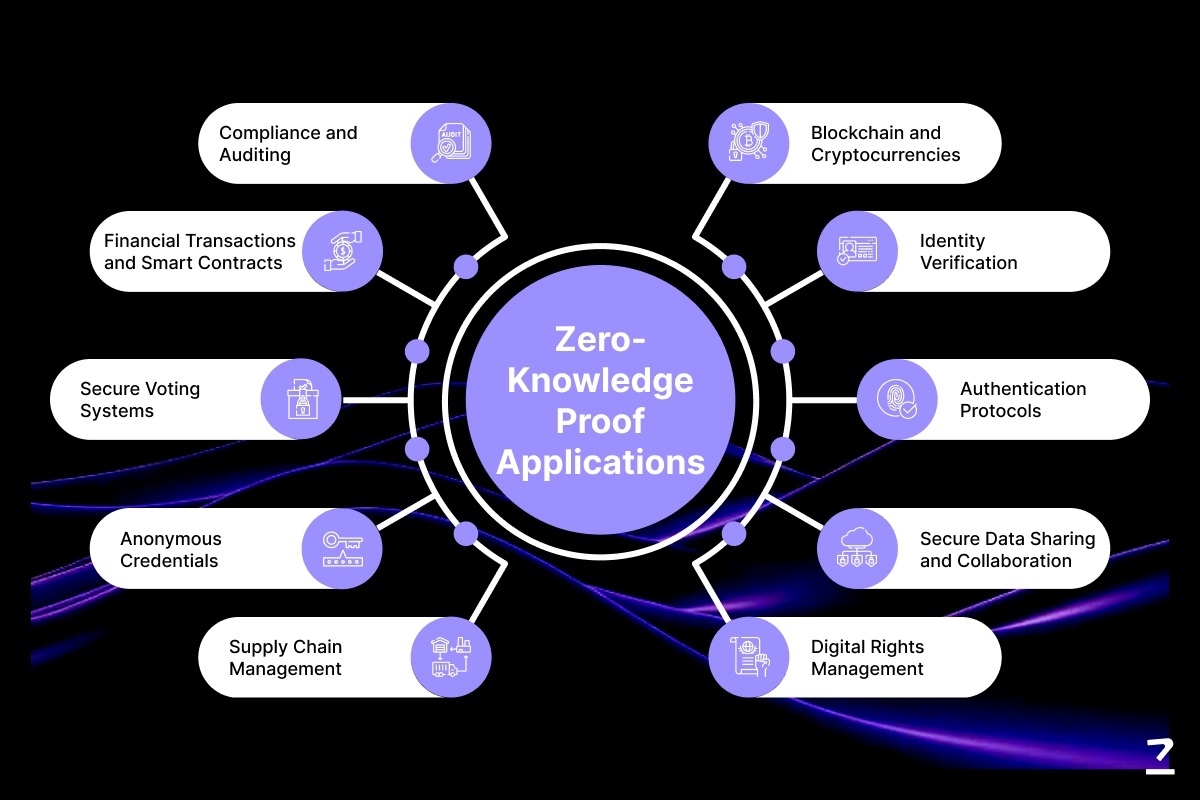
Top Use Cases of ZK Credentials
The value of zkp-based identity systems becomes clear when you look at where they are already being applied—or should be.
In Web3 apps, zk credentials can power gated access to token-gated communities, allow DAO voting without linking wallets to personal data, and enable fair airdrops where eligibility is verified without doxxing users. You prove what’s needed and nothing more.
In DeFi, they can support KYC-compliant onboarding without exposing sensitive user data. Users can prove they meet jurisdictional or regulatory requirements without submitting full documents to every new platform. This creates a balance between privacy and compliance.
For enterprises operating across borders, zk credentials offer a cleaner way to meet local laws and industry standards. Whether it's workforce verification, supplier audits, or customer onboarding, cryptographic identity systems reduce paperwork and improve security.
Beyond finance, sectors like healthcare, education, and supply chain are also beginning to explore ZK-based systems. In healthcare, you could prove vaccination status or insurance coverage without sharing your full medical record. In education, diplomas and certifications can be issued as verifiable credentials, instantly provable but tamper-proof.
All of this aligns with what many businesses now seek from enterprise blockchain solutions—privacy, automation, and trust. ZK credentials deliver all three, with the added bonus of user control built in from day one.
Building ZK Identity Systems - What Projects Should Know
Building a ZK-based identity system is not just about choosing the right cryptography. It is about understanding how people interact with identity across apps, wallets, and protocols—and designing a flow that keeps both privacy and usability intact.
For most projects, the challenge is not the concept. It is the execution. Integrating zk credentials into a product requires experience in smart contracts, verifiable credential frameworks, wallet integrations, and ZK libraries like Circom or SnarkJS. You are dealing with both on-chain and off-chain components that need to work seamlessly.
You also need to consider what your system needs to verify. Will you issue credentials yourself or accept them from other trusted issuers? Will your contracts verify proofs on-chain, or will you opt for off-chain verification with on-chain attestations? These design decisions affect scalability, gas fees, and user experience.
From a compliance angle, ZK identity systems can help projects meet regulatory expectations without over-collecting user data. But that only works if the system is built with care. Many projects try to skip this step and end up with broken flows or risky shortcuts.
This is where working with an experienced blockchain development company makes a difference. At Codezeros, we help startups and enterprises design privacy-first systems that actually work in production. Whether you need KYC verification, DAO participation logic, or token-gated access, we can help architect the right flow.
If you are serious about bringing user-controlled identity into your Web3 product, now is the time to build it right.
How Codezeros Helps Build ZK-Powered Identity Infrastructure
At Codezeros, we work at the intersection of privacy, trust, and cutting-edge blockchain technology. Our team has been helping forward-thinking businesses and startups build custom zk credential systems that align with both regulatory standards and user expectations.
Whether you are building a DeFi platform, an enterprise-grade compliance tool, or a public-facing dApp, we help you design a decentralized identity solution that works in the real world. Our approach balances cryptographic accuracy with practical usability, so your product stays secure without losing users to complexity.
We offer full-stack support for implementing zero knowledge proofs, verifiable credentials, smart contract infrastructure, and wallet integrations. From architecture to deployment, we ensure every part of your zk system is optimized for performance, privacy, and scale.
As a trusted blockchain development services provider, we focus on compliance-first and privacy-first design, helping you future-proof your identity stack while staying aligned with local and global standards.
Privacy Is Not Optional in Web3
If you are exploring enterprise blockchain solutions or want to bring a secure, trustless identity to your users, talk to us. We can help you build it right from the start.
Privacy Is Not Optional in Web3
As Web3 continues to evolve, the way we handle identity cannot be an afterthought. The future of online interaction demands more than access; it demands privacy, ownership, and trust.
zk credentials offer a path forward, where identity can be verified without exposing personal data. They are not just a technical upgrade; they are a shift in how we think about web3 identity management.
If your project involves users, access control, or compliance, it is time to start thinking in terms of privacy-preserving identity. Zero-knowledge is not just for the protocol layer anymore. It is a tool for building smarter, safer applications.
Explore how your team can integrate zk credentials into your stack, with the right partner by your side.
Post Author
Vivek is a passionate writer and technology enthusiast with expertise in blockchain development. As the lead writer for Codezeros, he aims to educate and inform readers about the potential of blockchain technology and simplify complex concepts to present them in an engaging manner for both technical and non-technical readers.
Design decentralized identity flows using zk cryptography with Codezeros
Skip the data leaks and legacy bottlenecks. Our experts help you design zero-knowledge-powered flows for authentication, KYC, and gated access that preserve privacy without compromising on usability or trust.



